To perform a cybersecurity risk assessment, start by identifying your critical digital assets, then evaluate potential threats and vulnerabilities to those assets. This structured approach helps uncover weaknesses before they turn into costly breaches.
At SubIT, we approach cybersecurity with the same precision as an in-house IT department, just more scalable. We know that security starts with consistency, responsiveness, and real experience. If you’re looking for clarity on where your risks lie, and how to fix them, you’re in the right place.
Key Takeaways:
- Identify and prioritize digital assets based on sensitivity and business value.
- Evaluate threats and vulnerabilities, then rank risks using a matrix.
- Apply targeted controls and continuously monitor for new threats.
What Is a Cybersecurity Risk Assessment?
A cybersecurity risk assessment is the process of identifying, evaluating, and prioritizing potential threats to your digital environment. It helps determine which assets are at risk, what vulnerabilities exist, and how to respond to reduce potential impact. Frameworks like NIST and ISO 27001 offer structured methodologies for this.
Why Risk Assessments Matter for Modern Businesses
According to IBM’s 2024 Cost of a Data Breach Report, the average global breach cost hit $4.88 million. Beyond the financial toll, there’s brand damage, customer trust erosion, and regulatory penalties. Regular risk assessments help businesses prevent breaches by identifying gaps early.
5 Steps to Perform a Cybersecurity Risk Assessment
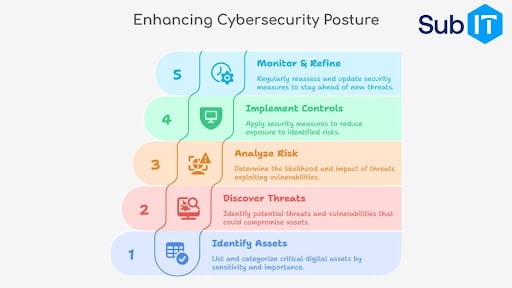
Step 1: Identify and Prioritize Digital Assets
Begin by listing all critical assets: servers, laptops, mobile devices, SaaS platforms, intellectual property, and employee data.
Types of Assets to Consider
- Physical assets (computers, routers)
- Data (customer records, financial info)
- Applications (internal tools, third-party apps)
- Users and roles
Use asset management tools or spreadsheets to categorize assets by sensitivity and business importance.
Step 2: Discover Threats and Vulnerabilities
Next, identify how each asset could be compromised. This involves:
- Threats: e.g., phishing, malware, insider abuse
- Vulnerabilities: e.g., outdated software, weak passwords
Common Cyber Threat Examples
Phishing remains the top attack vector, followed by ransomware and zero-day exploits. Insider threats are often overlooked but can be equally damaging.
Vulnerability Scanning Tools
Use tools like Nessus, Qualys, or SubIT’s managed scans to detect exposures automatically.
Step 3: Analyze Risk Likelihood and Business Impact
Determine the probability of each threat exploiting a vulnerability and the potential damage.
How to Build a Risk Matrix
Create a simple grid: Likelihood (Low to High) vs. Impact (Minor to Severe). Plot each risk to determine priority.
Quantifying Financial and Operational Impact
According to IBM, breaches involving stolen credentials took an average of 292 days to detect and contain. Time equals money. Consider downtime costs, compliance fines, and customer churn.
Step 4: Implement Security Controls
Apply protections to reduce your exposure. Prioritize controls for high-risk areas.
Technical, Administrative, and Physical Controls
- Technical: Firewalls, MFA, endpoint detection
- Administrative: Security policies, training
- Physical: Device locks, secure rooms
Prioritizing High-Risk Mitigation
Fix high-likelihood/high-impact risks first, then address medium tiers.
Step 5: Monitor, Audit, and Refine Regularly
Security isn’t static. Reassess regularly to stay ahead of new threats.
Setting a Continuous Risk Monitoring Schedule
Perform quarterly audits, monthly patch checks, and annual assessments.
Involving Your Team in Ongoing Cyber Hygiene
Train staff regularly and reward secure behavior. SubIT clients see stronger results when everyone shares responsibility.
Ready to Find and Fix Your Cybersecurity Gaps?
A solid cyber risk assessment is just the beginning. At SubIT, we help businesses not only pinpoint threats but build long-term protection into their everyday operations. Our team can help you stay secure at scale, with people-first support that works across locations and time zones.
Contact our team today and let’s make your cybersecurity proactive, not reactive.









